1. Role based security control:
- By default, the business objects in your application are accessible to all users that can access the application.
- To secure the data stored in objects, you can use user roles to restrict a user’s access to view, create, update, and delete operations by configuring role-based access for each operation. Users can only perform the operations and interact with the business objects associated with the role that the user has been assigned.
- To allow anonymous access to the data in a business object, for each operation you must explicitly set the permissions granted to the Anonymous User authentication role.
To enable role-based security for a business object:
Select the business object you want to secure >> Open the Security tab of the business object.
When configuring security, you can allow external clients to access the business objects in your application through their REST endpoints. For example, you might want an external service like Process Automation to update a business object after a process is complete, say change a status field from "requested" to "approved".
To do this, you need to retrieve the API for the catalog of endpoints exposed by your application's business objects, found in the Catalog API panel in the Business Objects tab of your application's Settings editor:
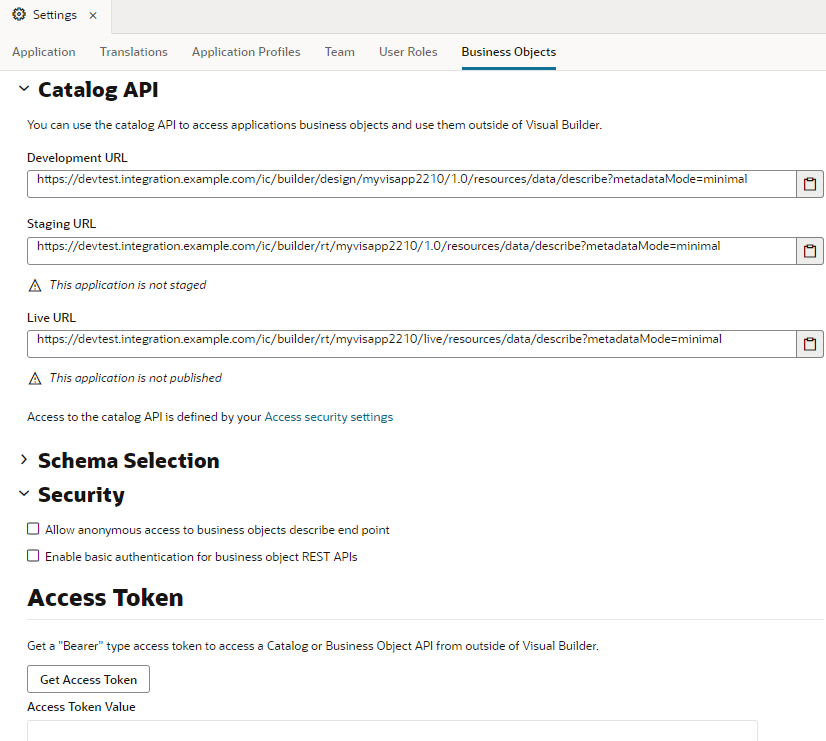
- Open the Business Objects tab in the visual application’s Settings editor.
- Under Security, select an authentication option:
- Allow anonymous access to business objects describe end point
- Enable basic authentication for business object REST APIs








No comments:
Post a Comment